Background
If you’ve ever tried to install Linux from scratch or with a distribution such as Arch or Gentoo you would have found the partitioning and boot loader setup to be a rather confusing mess of different standards, compatibility problems and issues, particularly with dual booting, even when using an installer there is still a chance things will not work as intended, additional features such as encryption, secure boot, fast boot and RAID further complicate matters, in this article I will attempt to simplify things somewhat, however I still recommend referring to the Arch and Gentoo wikis for the finer details.
BIOS and UEFI
The Basic I/O System (BIOS) is a memory chip on the motherboard that contains the code used to perform initialisation of hardware, provide basic software services and configuration used during the boot process, a lot of this was standardised way back in the 80’s so as you might expect the BIOS is now being phased out in favour of the Unified Extensible Firmware Interface (UEFI), this is a much more modern replacement that was introduced in 2006, as of today all consumer level computers support UEFI.
UEFI shares a lot of similarity with the BIOS and includes backwards compatibility, it provides a number of new features such as enhanced user configuration, support for modern technologies such as secure boot and the UEFI boot process, any preinstalled system since Windows 8 uses it by default, UEFI comes in 32 bit (known as IA32) and 64 bit variants, the former is somewhat rare so if you have a relatively modern computer it’s almost certainly 64 bit UEFI.
Partition Table
The partition table is a data structure that tells software how the drive has been partitioned, the original partition table is called the Master Boot Record (MBR) since it contains the master boot loader along with the partition table, this can register a maximum of four primary partitions which can contain their own boot loader, one of these can be replaced with an extended partition which may contain any number of logical partitions, the first 512 byte sector1 of a drive contains the boot loader (446 bytes) along with the partition table (64 bytes) plus a 2 byte signature, due to the very small size it’s typical for the boot loader to read a partition and execute a larger boot loader, a process known as chain loading.
Due to the significant limitations with the MBR partition table a new one was introduced around the time of UEFI called GUID Partition Table (GPT), this allows for much larger disks (> 2 TB) as well as up to 128 partitions, it also includes redundancy and error checking with a copy of the GPT being placed at the end of the drive. For backwards compatibility and to avoid damage from software that is not GPT aware a MBR2 is placed in the first sector of the drive.
Boot Process
For a BIOS system after completing the Power On Self Test (POST) which checks and initialises the hardware, it looks for a disk with a valid MBR, this is then executed, BIOS is capable of booting both MBR and GPT.
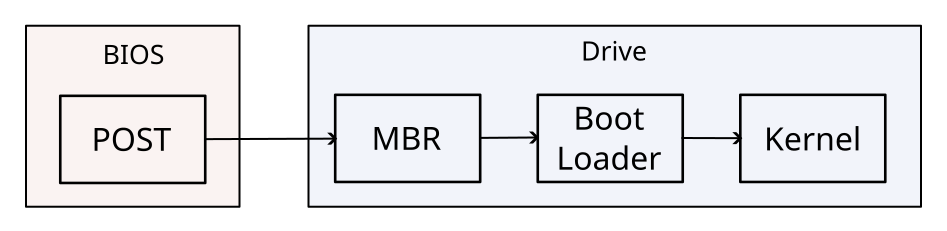
UEFI provides support for the legacy BIOS boot process using the Compatibility Support Module (CSM) which can be disabled if so desired, UEFI is almost always used with GPT, after the POST stage UEFI looks in its own Non-Volatile Random Access Memory (NVRAM) which contains the boot entries that tell it where to find boot loaders along with other EFI variables and applications.
Unlike BIOS it can read some partitions directly, boot loaders and other UEFI applications are stored in the EFI System Partition (ESP) which is normally a FAT32 partition of at least 100 MiB, only one of these is allowed per drive, boot loaders are stored as normal files, for example the Windows boot loader is /EFI/Microsoft/Boot/bootmgfw.efi, for removable drives that don’t have an entry in the NVRAM the boot loader is stored at /EFI/Boot/bootx64.efi (bootia32.efi for 32 bit).
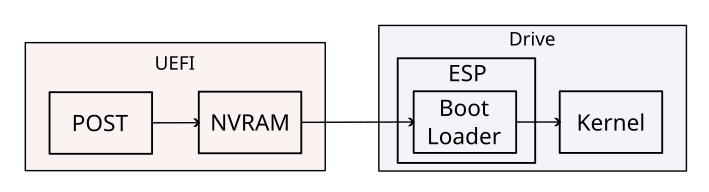
Once the boot loader is executed things proceed mostly the same as with BIOS.
This gives us four possible combinations:
- BIOS / MBR
- BIOS / GPT
- UEFI / MBR
- UEFI / GPT
Option 2 is not recommend if you’re trying to dual boot since Windows never uses this setup, option 3 is not recommended even though it may technically work.
BIOS/MBR Setup
This is an example of a simple BIOS / MBR setup with a single root partition:
| Mount Point | Partition Type | Recommended Size |
| [SWAP] | SWAP | 4 GiB minimum |
| / | Linux Filesystem | Rest of drive |
Installing GRUB for example is done with:
grub-install --target=i386-pc /dev/sdX
grub-mkconfig -o /boot/grub/grub.cfgWhere /dev/sdX is the root partition, or /boot partition if a separate one is used.
BIOS/GPT Setup
The only real difference here is that GRUB requires a little room at the start of the drive to store part of the boot loader, which would normally be stored in the gap between the MBR and the first partition, since the GPT partition table is bigger we need a dedicated partition for this.
| Mount Point | Partition Type | Recommended Size |
| BIOS Boot Partition | 1 MiB | |
| [SWAP] | SWAP | 4 GiB minimum |
| / | Linux Filesystem | Rest of drive |
Installation otherwise remains the same as BIOS/MBR, note that the BIOS boot partition must not be formatted as anything.
UEFI/GPT Setup
| Mount Point | Partition Type | Recommended Size |
| /boot or /efi | EFI System Partition | 1 GiB |
| [SWAP] | SWAP | 4 GiB minimum |
| / | Linux Filesystem | Rest of drive |
The ESP should be formatted as FAT32, where you mount it has a significant impact, mounting it to /boot makes maintenance and updates easier however there is a potential risk that other operating systems may screw with the ESP in a way that breaks your system, mounting it to /efi eliminates this risk and allows for a smaller partition since it only needs to store the boot loader, personally I recommend the former option for the sake of simplicity, besides GRUB you should have efibootmgr and os-prober installed.
Installation of GRUB is done with:
grub-install --target=x86_64-efi --efi-directory=esp --bootloader-id=GRUB
grub-mkconfig -o /boot/grub/grub.cfgReplace esp with either /boot or /efi, use i386-efi if you have 32 bit UEFI.
Alternatively rEFInd may be a better choice of boot loader than GRUB particularly if you want more advanced features, other options include EFISTUB and systemd-stub.
Note: It may be advisable to install as a removable disk, this provides protection should the EFI variables in NVRAM become damaged or you have to move the drive to another computer and want it to remain bootable, this can be done by adding the removable flag to grub-install.
Dual Booting with Windows
Dual booting Windows has many traps for beginners so I don’t generally recommend it, but if you really want to do it you need to understand some limitations based on the Windows version you want to use:
- Windows 8/8.1 and 10 32 bit only support booting from IA32 UEFI/GPT or BIOS/MBR
- Windows 8/8.1 and 10 64 bit only support booting from UEFI/GPT or BIOS/MBR
- Windows 11 supports 64 bit UEFI/GPT only
To ensure compatibility you should use the same boot method on both Windows and Linux, regardless if they are on different drives or not.
Generally it’s recommended to install Windows first then Linux but it can be done the other way around, Windows installed in UEFI mode will create an ESP if one doesn’t exist, this is by default too small to mount to /boot so you will have to resize it, or create the partition layout yourself, if possible I would strongly recommend having Windows and Linux on separate drives to make life a bit easier.
Before you attempt anything read carefully through this wiki page and make sure you have enough time to deal with problems, once you’ve done it a few times it isn’t that difficult.